Hacking Industry 4.0
The danger in Industrial Internet of Things technology is that data so conveniently shared can also be stolen or corrupted.
#iot
Cyberattacks lie in a dark shadow behind the shiny promise of Industry 4.0: The same technology that allows data to be shared and studied inside an enterprise may be accessed from outside to steal or corrupt that data.
“The interconnectedness of Industry 4.0-driven operations, along with the escalating deployment of industrial internet-of-things (IIoT) devices, has created a massive attack surface for cybercriminals to exploit,” says Chris Morales, head of security analytics at cyber security company Vectra (vectra.ai). “Many factories connect IIoT devices to flat, unpartitioned networks that rely on communication with general computing devices and enterprise applications.”
Manufacturers used to rely on customized, proprietary protocols, which made mounting a cyberattack difficult, Morales notes. The conversion from proprietary protocols to standard protocols makes it easier to infiltrate networks. IIoT devices can then be used as a beachhead to launch an attack: “Once an attacker establishes a foothold in IIoT devices, it is difficult for network security systems to identify the backdoor compromise.”
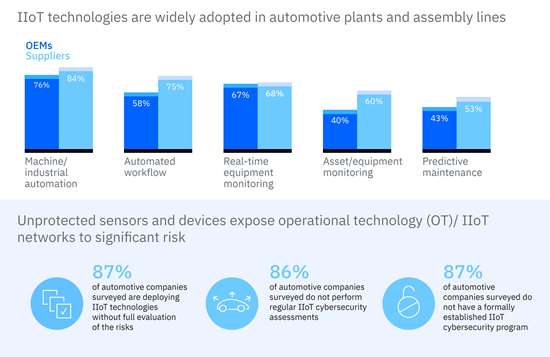
The IBM Institute for Business Value (ibm.com) surveyed manufacturers and found that a worrisome percentage (87 percent) of automotive companies are implementing IIoT technologies in plants and assembly lines without fully evaluating risk or preparing effective responses. However, the same survey revealed the best practices of the “top performing” companies in the other 13 percent. Those include:
- Applying user privacy controls to IIoT devices.
- Using authentication to verify users on IIoT devices.
- Defining clear service-level agreements SLAs for security and privacy.
- Inventorying all authorized and unauthorized software.
- Using devices with built-in diagnostics.
- Automating the scanning of connected devices.
- Securing device hardware and firmware.
- Using advanced behavioral analytics for breach detection and response.
- Using AI technology to enable real-time monitoring and response.
Automated Field Agents
As mentioned in the final two bullet points above, effective cyber defense technology now uses artificial intelligence (AI) and behavioral analytics to automate a sophisticated and, more importantly, active defense posture.
One can imagine a traditional cyber defense system as being the equivalent of a sentry at the gate: When a stranger approaches, the sentry asks “who goes there?” If the right response is given, the stranger can pass. If not, it’s rejected. The sentry knows how to identify “good-guy” responses, and that’s all he needs to know to keep danger at bay.
That’s no longer enough, given the speed and sophistication with which cyberattackers now can assail those guard posts. Now, attackers can try thousands of different approaches at a multitude of entry points in a short time—and if one does get past a sentry, it can hide within the system, disguised, while performing its nefarious mission.
So, instead of passively waiting for and hoping to detect a cyberattack, modern systems now actively look for them and study what they find. They’re less like sentries and more like counterintelligence field agents.
Vectra’s Cognito platform, for example, uses AI with continuous-learning behavioral models to seek and find hidden attackers before they can do damage. The system learns and exposes the cyberattacker’s behaviors, whether the attack comes from cloud and data center workloads, communication equipment such as computers, phones and tablets, or IoT-enabled devices such as CNC equipment—leaving attackers with nowhere to hide.
National Defense
To better protect themselves, it behooves companies to get beyond an “every-enterprise-for-itself” mindset and work with each other to develop solutions for their mutual cyber defense, particularly against foreign bad actors. So says Sridhar Kota, a director at The Alliance for Manufacturing Foresight (MForesight; mforesight.org). He suggests ways government, industry, and academia should work together, including:
Building partnerships: “There’s a need for new third-party partners to coordinate better sector-wide strategic planning and training programs, including new ‘boot camps’ for preventative action and crisis management.”
Investing in R&D: “There’s a need for research around near-term needs—like automated risk assessment tools, tools to audit the extent of attacks, and effective validation programs for parts and data—as well as long-term needs like defining IT and OT [operational technology] functions and consistent standards and integration requirements for diverse players in a supply chain.”
Sharing information: “Manufacturers need an Information Security Advisory Council or similar mechanism to facilitate fault-free, anonymous sharing on incidents, threats, vulnerabilities, best practices, and solutions. Existing ISACs can provide useful models.”
“Business and government need to get together and think strategically about cyber defense,” says Kota.
RELATED CONTENT
-
VW Connects with Amazon and Siemens on Manufacturing
Amazon is increasing its penetration into the auto industry not just through things like Alexa and its multi-million-dollar investment in EV developer Rivian, but also with its Amazon Web Services (AWS), which will be used for its “Volkswagen Industrial Cloud,” which will combine the data from all of the machinery and equipment in the company’s 122 facilities.
-
Tools You Can Use
Here are a few useful developments for your manufacturing operations, whether it is making components for electrical systems or camshafts or more.
-
The Network and the Sensor
The smart-factory world of digital manufacturing is coming, and manufacturing-technology developers are eager to help you be ready.